In today’s digital age, every organization understands the importance of securing their applications and systems against unauthorized access and cyber-attacks. The rise of new technologies and the ever-evolving IT landscape have necessitated the implementation of a robust Identity and Access Management (IAM) system accompanied by a Role-Based Access Control (RBAC) framework.
In this blog, we will dive into essential IAM and RBAC best practices that organizations can adopt to ensure secure application access and robust IT risk management. We will explore the importance of protecting applications/systems, the importance and principles of IAM, RBAC, business roles, the Principle of Least Privilege (PoLP), defining access control policies, and sustainable IAM/RBAC integration.
Why Protecting Applications & Systems is Critical
Securing an organization’s applications and systems against unauthorized access is sacrosanct. Due to the sensitive nature of the data within these systems, a data breach can have far-reaching consequences that can result in legal and financial penalties, loss of customer trust, and ultimately affecting brand reputation. A strong IAM/RBAC framework helps keep cyber threats at bay and minimize the impact of data breaches.
In today’s rapidly evolving digital landscape, data security and privacy have become paramount concerns for organizations of all sizes. Managing who has access to sensitive information and how they access it is a critical aspect of safeguarding valuable assets. This is where Identity and Access Management (IAM) comes into play. Let’s delve deeper into IAM and explore a few of its key components: Role-Based Access Control (RBAC), defining business roles within an organization, and how IT Risk management plays a crucial part.
What is Identity & Access Management (IAM)?
Identity and Access Management (IAM) is a comprehensive framework that empowers organizations to control and administer the access of individuals, including employees, partners, customers, and other stakeholders, to their applications and data resources. In essence, IAM is the digital gatekeeper which ensures that the right individuals gain access to the right resources, at the right time, and under the right conditions, whilst abiding by applicable regulatory practices. Furthermore, it is a critical component in the ongoing battle against external threats and cyberattacks, making it an indispensable tool in the modern business landscape.
Within the broader scope of IAM, Role-Based Access Control (RBAC) serves as a vital subset. RBAC is a method of managing access based on users’ roles within an organization. In simpler terms, it’s about providing access to individuals based on their specific job functions or responsibilities. This approach brings about two notable benefits:
1. Enhanced Efficiency – Imagine a scenario where an HR manager, a sales director, and an IT technician all require access to various parts of the organization’s data. Without RBAC, each individual might need to request access permissions separately, taking unnecessary internal resources, time and waiting for ticket approval. With RBAC, however, access is streamlined and automated based on predefined roles. RBAC ensures that individuals gain efficient access to their relevant role-related resources in order to perform in their position most effectively.
2. Reduced Security Risks – RBAC plays a pivotal role in bolstering cybersecurity efforts. By assigning access permissions according to job roles, organizations can limit access to sensitive data which in turn, reduces the risk of unauthorized access or data breaches. This approach ensures that employees can only access information that is relevant to their job responsibilities, minimizing the potential damage that could occur if access is granted indiscriminately.
RBAC & The Significance of Business Roles
In the context of IAM and RBAC, business roles refer to the hierarchy levels defined within an organization. These roles are instrumental in classifying tasks and responsibilities into specific groups of users. Typically, this classification occurs at the organizational structure level, with top-level executives having the highest security clearances compared to employees at lower organizational levels.
Business roles foster accountability within an organization ensuring that individuals are accountable for their actions and the data they handle. By establishing clear business roles, organizations can effectively mitigate the risk of unauthorized access. Business roles align closely with RBAC, ensuring that users are granted access permissions that align with their job functions. This alignment acts as a barrier against unauthorized access, reducing the potential for data leaks and security breaches. In cases of security breaches or data mishandling, it becomes easier to trace the source of the issue and take appropriate measures.
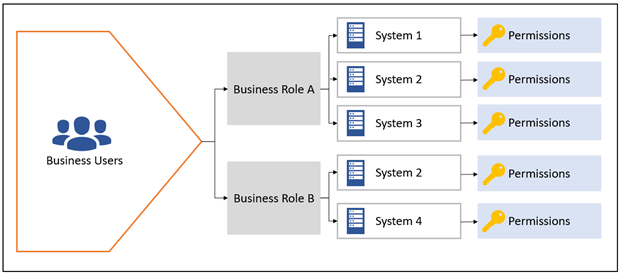
At a high level, when users are assigned a role, they are granted access to pre-authorized systems, applications and permissions which have been mapped out based on the job function and its required resources. When designing business roles, in addition to leveraging the Principle of Least Privilege which is detailed below, users are still be able to request further access permissions through your organizations regular ticketing platform (e.g., SNOW, JIRA, SolarWinds, etc.) and therefore will follow the same approval workflows.
Identity and Access Management (IAM) is a cornerstone of modern cybersecurity practices, and within IAM, Role-Based Access Control (RBAC) is a powerful tool for managing access efficiently and securely. Additionally, defining business roles is an essential step in ensuring accountability and reducing the risk of unauthorized access within organizations. By embracing these practices, organizations can fortify their data security defenses and operate with greater confidence in an increasingly digital world.
The Principle of Least Privilege (PoLP)
The PoLP dictates that users should only have access to the minimum permissions necessary to perform their duties. As such, organizations should classify users based on their job functions and restrict access to only what is essential for their roles. This reduces the attack surface and limits potential damage in case of a breach.
Furthermore, it’s not enough to simply decide on the minimum permissions a user needs; these permissions also need to be regularly reviewed to ensure they are still appropriate for the user’s role. As individuals progress through the company, their responsibilities and required access may change. Regular audits of user access can help uncover any potential over-provisioning of permissions, thereby reducing risk and maintaining adherence to the PoLP.
Another critical aspect of implementing PoLP effectively is the segregation of duties. This involves splitting responsibilities among multiple individuals to prevent any one person from having too much control or access. This serves as a form of internal control designed to prevent errors and fraud, enhancing the overall security posture of the organization.
Tailoring Access Control Policies
Effective access control policies are the backbone of a secure IAM/RBAC system. These policies determine who can access specific resources under well-defined conditions, and they are essential for maintaining data security and integrity. Let’s explore this crucial aspect in more detail:
Organizations should begin by crafting comprehensive access control policies that align with their security goals and regulatory requirements. These policies should clearly define:
User roles and responsibilities: identify various roles within the organization and specify their access needs.
Resource classification: categorize data and resources based on sensitivity levels.
Conditions and constraints: define circumstances under which access is granted or denied (e.g., time of day, location, device type).
Exceptions and approvals: establish procedures for granting exceptions to the standard policies, ensuring that exceptions are carefully evaluated and approved.
Revocation procedures: outline the steps for revoking access when an employee leaves the organization, and their access to all assets should be revoked.
Sustainable IAM/RBAC Integration
The effectiveness of an IAM system hinges on the continuous training of employees and promotion of sustainable practices. Here’s how organizations can achieve this:
Continuous Training: employees should receive ongoing training to understand the importance of their roles within the IAM/RBAC framework. This includes educating them on best practices for access management, data security, and compliance. Regular training sessions can help keep employees informed and vigilant.
Adapting to Change: job roles and responsibilities often evolve. It’s crucial to update system access and permissions as these changes occur. This ensures that employees have the appropriate level of access to their current roles and responsibilities. Timely updates also help prevent unnecessary access, reducing security risks.
Regular Testing: periodic testing of the IAM/RBAC system’s robustness is essential. Organizations should conduct vulnerability assessments, penetration testing, and simulated cyberattack exercises to identify weaknesses and vulnerabilities. These tests help in fine-tuning the system’s security measures and ensuring its resilience against evolving threats.
Continuous Monitoring: proactive monitoring of the IAM/RBAC system’s performance is vital to staying ahead of potential cyber threats. Real-time monitoring and alerting can help organizations detect suspicious activities or access attempts. Continuous monitoring ensures that any anomalies are promptly addressed, minimizing the risk of data breaches.
Modern Authentication Mechanisms: to enhance security, organizations should consider adopting modern authentication mechanisms, such as Multi-Factor Authentication (MFA). MFA requires users to provide multiple pieces of evidence of their identity before granting access. This could include something the user knows (like a password), something the user has (like a soft/mobile token), and something the user is (like a fingerprint or other biometric method). Incorporating MFA within the IAM/RBAC framework significantly decreases the likelihood of unauthorized access, even in instances where user credentials have been compromised.
A Final Thought
In order to ensure maximum security, it’s important to understand that security is not a one-time achievement but an ongoing process. The exponential growth of the digital landscape reflects an influx of threats, which highlights the urgency for organizations to establish robust IAM and RBAC systems that are adaptable and flexible to address emerging challenges.
Optimus SBR Technology & Data Services Practice
Within our Technology & Data Services Practice at Optimus, our goal is to help our clients fill in the white space and align business and technology teams to ensure success. We move beyond the provision of resources and deliver innovation – we seek out practice efficiencies, leverage tools and automation where appropriate, and bring a bold, problem-solving orientation to our work because ultimately, technology needs to deliver the right things the right way.
Contact us to learn more about our Technology & Data Services, and how we can help you on your IAM & RBAC journey.
Doug Wilson, Senior Vice President and Technology & Data Practice Lead
Doug.Wilson@optimussbr.com
Paul Smith, Vice President, Management Consulting Services
Paul.Smith@optimussbr.com

Optimus SBR Celebrates 6 Consecutive Wins as 2024 Best Workplaces™ in Professional Services
Our commitment to a people-first approach has been central to being recognized in 2024 for the sixth time as one of the Best Workplaces™ in Professional Services and the key to our overall success.

12 Best Practices to Increase Cross-Team Collaboration and Enhance Organizational Alignment
Enhancing cross-team collaboration drives innovation, optimizes resources, improves overall performance, and ensures every part of your organization works toward the same goals.

Enhancing Your Data Strategy for Success: The Power of Metadata
Metadata goes beyond just aiding in data retrieval. It ensures your data is secure, compliant and, most importantly, understood consistently by everyone in the organization.

Optimizing Language Translation Strategies: Beyond Compliance to Enhanced Operational Efficiency
The introduction of Quebec’s Bill 96 in Canada underscores the necessity for comprehensive translation strategies. Integrating machine translation technologies helps meet regulatory requirements while enhancing translation speed, cost efficiency, and operational effectiveness.

How to Manage Gen Z: 16 Strategies to Engage and Retain Young Talent
These practical strategies lead to a workplace that is better aligned with the values and expectations of Gen Z employees, ensuring that your efforts to attract and retain Gen Z talent are both successful and sustainable.

How to Measure the Success of Learning and Development: 12 Important Metrics to Evaluate
Quantifying the success of L&D training programs can be challenging. Learn about selecting and measuring the right metrics to determine whether your training efforts are truly making an impact.



